CryptoLocker Decryption Service – helping to Decrypt Encrypted Files
As of 1st November 2013 I know there are lots of people are affected by CryptoLocker virus and there are plenty of article on web talking about how to remove the virus, but what about the files that are already encrypted?
I have been bombarded with emails, is there anyway to decrypt these file or How to decrypt the CryptoLocker encrypted files. To decrypt the encrypted files you will need to find your Public Key and Private Key.
Below is an image from Microsoft depicting the process of asymmetric encryption.
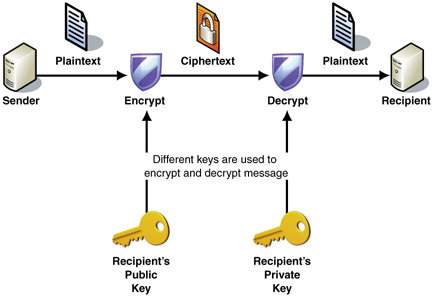
The bad news is decryption is impossible unless a user has the private key, as it is stored on the cybercriminals’ server.
Infected users also have a time limit to send the payment. If this time elapses, the private key is destroyed, and your files may be lost forever.
Files targeted are those commonly found on most PCs today; a list of file extensions for targeted files include:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx
Public key is generally located in your file and Private Key is located in CryploLocker Control Server, only way to get get the Private Key is to find the Control Server and pay the ransom. After many hours of research, I have managed to contact CryptoLocker control server and managed to help others purchasing Private Key for the encrypted file for who never had any shadow copy or backup of files. After downloading Private Key from CryptoLocker Control server at a cost, very high cost, up to 9BTC (equivalent to £2200 or $3,500) then I did managed to decrypt these files.
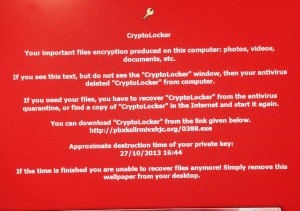
Let’s say that your computer is infected with the malware, but you decide not to pay up. You remove the malware and try to restore your files from backups or Shadow Copy. However, you might come to realise that your choice isn’t the best one. Your backups might be broken or infected, or you might not have enough backups, so you come to the conclusion that it would have been best to pay the fee, in the first place.
A new malware warning was issued this week alongside a Cryptolocker virus removal tool and decryption service. Cryptolocker, new malware running rampant on the web right now, has taken a multitude of users computers for ransom, demanding those infected with the virus to pay up or see their encrypted files disappear forever. However, it seems things just getting worse, as a new warning for the malware has emerged, and ransom is getting higher. Not only are the makers of Cryptolocker demanding your money for a private key to decrypt your encrypted files, if you don’t pay up before the 72 hour time limit, the amount is upped from two or three hundred dollars, to 3,500 or more.
See the screens below how the process work, you will not be able to access the control server from normal web browsers.
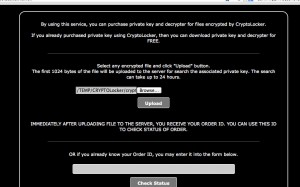
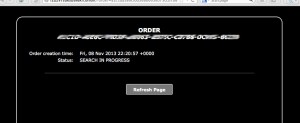
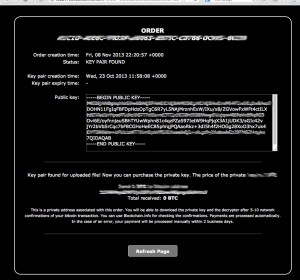
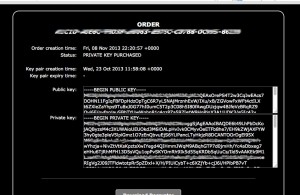
This service allow you to purchase private key and decrypter for files encrypted by CryptoLocker. If you already purchased private key using CryptoLocker, then you can download private key and Decrypter for Free,” reads a notice posted on the website. However, the trick is that it’s far more expensive to use the Decryption Service than if you had paid up in the first place. When a computer is infected with CryptoLocker, victims are asked to pay 2 Bitcoins to have their files restored. On the other hand, using this service costs 10 Bitcoins or more. Of course, you shouldn’t pay up in case your computer is infected with CryptoLocker. However, there might be some scenarios in which victims simply don’t have any other choice. On the other hand, the best thing to do is avoid falling victim in the first place. Keep backups of your most important files, keep your antivirus and other pieces of software up to date, and avoid accessing links or email attachments that look suspicious.
I do not recommend anyone paying the ransom but at a last resort if you decided to pay then I can try to help with the process. I have setup a CryptoLocker test lab with an email address “xxxx at gmail dot com” for anyone need help on decrypting their file. All I need is one of the encrypted file emailed to me at “xxxx at gmail dot com” , once I have the file then I can try to contact one of control server and fine the Public Key & date of Key Pair was crated, and how much it will cost to get Private Key.
I do not ask for any money for my service to contact the CryptoLocker control server and upload your file to search for private key, if the match is found I will email you back with Public Key & date of Key Pair was crated & cost, this process can take up to 24hr-48hr. [Due to time constrain I have stopped taking any further cryptolocker query]
Please make sure you have tried everything before sending the files, because it can be very expensive, I have seen ransom paid up to £2500 ($3850).
Have you tried volume shadow copy or shadow explorer to restore you can check my blog posted on http://blog.shiraj.com/2013/10/shadowexplorer-how-to-use/ this will save you lots of money.
— —– —
UPDATE [December 10, 2013: 17:50]: Unfortunately, I have lost my connection to cryptolocker server I believe it’s been take down. Until I track another command control server I can’t help anyone with getting the private key. I will post any further update on this page.
UPDATE [December 11, 2013: 10:50]: I have connection to another command control server.
Categorised as: blogmail, Hardware/Software, Microsoft, Networking, Password, Recovery, Server OS
“xxxxxx at gmail dot com”Send me one encrypted file I will check.File was sent. Thanks for checking it.
Hello,
I’ve believe I have gotten the cryptolocker virus but there’s something different than what I’ve seen described. I only have a text doc that explains how to pay to get my files back. There is no pop up or wallpaper with a link. I downloaded the tor browser to access the cryptolocker decryption service site. When I upload any encrypted files it tells me they are not encrypted. All of my files end in .cryptolocker. Have you seen this before? What should I do now?
Yes I have seen this. This is different group of crypto locker team, they don’t have website to upload your file to check. In the text file you will see your transaction code ref to send bitcoin to their bitcoin address with ref, once they get the payment and verified by bitcoin network an email with attachment of decrypter get send to your email address.
Shiraj,
I sent an email the other day, I’m not sure if you received it. I sent it to the email address at the top.
I have files that were encrypted but the virus was cleaned and no one wrote down the info to decypt the files.
Do you know what options are available? Can I still can a decryptor?
Thank you for any assistance you can provide.
Hello shiraj My father`s laptop was infected with encryptdefense and inside it he has files of his work. Would you mind helping me? I`m desperated
I had to pay the ransom, I have the encryption keys and I downloaded the decryption tool. Unfortunately the decryption tool is carrying a virus as well… Luhe.Fiha.A
Is there another utility to decrypt the files using the keys?
This is the only way to decrypt, you should copy files to isolated PC then run this decrypter. It is normal for virus software to see this as virus because this is what it’s using to decrypt.
We have paid ransom, but the page on onion went offline after we proceeded with payment is that normal? also can i still send you an file that is locked?
May be the server have been taken down, this has happened before check after 24hr.
We just got cryptolocker on one of our workstations. The problem is that encrypted files on our network common drive. Two questions, will the decrypting see the infrcted files on the network? I don’t want to pay and not have it work. Please help me anyway you can. Our backup common drive data is infected too.
could I please send you a file that is encrypted to see if there is anything that can be done?
I paid the ransom as I desperately need my files and after a few hours got a message that the payment processing server could not be reached and to try to connect to Internet which I was connected all the time. After 24 hours nothing has changed. I have disabled the firewall and even tried different connection (WiFi) – nothing helped. Finally I shut down the computer and took it home where I connected it to my home router, but the processing window is not coming back. I only have the red background. How do I restart the damned Cryptolocker to try to run the decryption? Please help.
I’ve succeeded to decrypt files, if someone needs help feel free to contact me at griskra(at)libero.it