CryptoLocker Decryption Service – helping to Decrypt Encrypted Files
As of 1st November 2013 I know there are lots of people are affected by CryptoLocker virus and there are plenty of article on web talking about how to remove the virus, but what about the files that are already encrypted?
I have been bombarded with emails, is there anyway to decrypt these file or How to decrypt the CryptoLocker encrypted files. To decrypt the encrypted files you will need to find your Public Key and Private Key.
Below is an image from Microsoft depicting the process of asymmetric encryption.
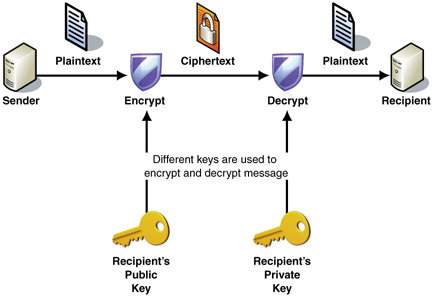
The bad news is decryption is impossible unless a user has the private key, as it is stored on the cybercriminals’ server.
Infected users also have a time limit to send the payment. If this time elapses, the private key is destroyed, and your files may be lost forever.
Files targeted are those commonly found on most PCs today; a list of file extensions for targeted files include:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx
Public key is generally located in your file and Private Key is located in CryploLocker Control Server, only way to get get the Private Key is to find the Control Server and pay the ransom. After many hours of research, I have managed to contact CryptoLocker control server and managed to help others purchasing Private Key for the encrypted file for who never had any shadow copy or backup of files. After downloading Private Key from CryptoLocker Control server at a cost, very high cost, up to 9BTC (equivalent to £2200 or $3,500) then I did managed to decrypt these files.
Let’s say that your computer is infected with the malware, but you decide not to pay up. You remove the malware and try to restore your files from backups or Shadow Copy. However, you might come to realise that your choice isn’t the best one. Your backups might be broken or infected, or you might not have enough backups, so you come to the conclusion that it would have been best to pay the fee, in the first place.
A new malware warning was issued this week alongside a Cryptolocker virus removal tool and decryption service. Cryptolocker, new malware running rampant on the web right now, has taken a multitude of users computers for ransom, demanding those infected with the virus to pay up or see their encrypted files disappear forever. However, it seems things just getting worse, as a new warning for the malware has emerged, and ransom is getting higher. Not only are the makers of Cryptolocker demanding your money for a private key to decrypt your encrypted files, if you don’t pay up before the 72 hour time limit, the amount is upped from two or three hundred dollars, to 3,500 or more.
See the screens below how the process work, you will not be able to access the control server from normal web browsers.
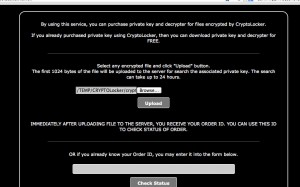
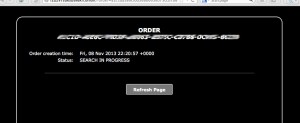
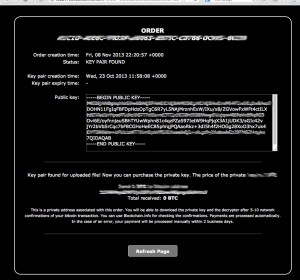
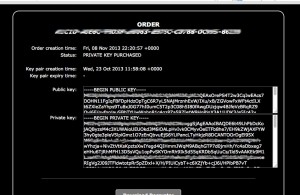
This service allow you to purchase private key and decrypter for files encrypted by CryptoLocker. If you already purchased private key using CryptoLocker, then you can download private key and Decrypter for Free,” reads a notice posted on the website. However, the trick is that it’s far more expensive to use the Decryption Service than if you had paid up in the first place. When a computer is infected with CryptoLocker, victims are asked to pay 2 Bitcoins to have their files restored. On the other hand, using this service costs 10 Bitcoins or more. Of course, you shouldn’t pay up in case your computer is infected with CryptoLocker. However, there might be some scenarios in which victims simply don’t have any other choice. On the other hand, the best thing to do is avoid falling victim in the first place. Keep backups of your most important files, keep your antivirus and other pieces of software up to date, and avoid accessing links or email attachments that look suspicious.
I do not recommend anyone paying the ransom but at a last resort if you decided to pay then I can try to help with the process. I have setup a CryptoLocker test lab with an email address “xxxx at gmail dot com” for anyone need help on decrypting their file. All I need is one of the encrypted file emailed to me at “xxxx at gmail dot com” , once I have the file then I can try to contact one of control server and fine the Public Key & date of Key Pair was crated, and how much it will cost to get Private Key.
I do not ask for any money for my service to contact the CryptoLocker control server and upload your file to search for private key, if the match is found I will email you back with Public Key & date of Key Pair was crated & cost, this process can take up to 24hr-48hr. [Due to time constrain I have stopped taking any further cryptolocker query]
Please make sure you have tried everything before sending the files, because it can be very expensive, I have seen ransom paid up to £2500 ($3850).
Have you tried volume shadow copy or shadow explorer to restore you can check my blog posted on http://blog.shiraj.com/2013/10/shadowexplorer-how-to-use/ this will save you lots of money.
— —– —
UPDATE [December 10, 2013: 17:50]: Unfortunately, I have lost my connection to cryptolocker server I believe it’s been take down. Until I track another command control server I can’t help anyone with getting the private key. I will post any further update on this page.
UPDATE [December 11, 2013: 10:50]: I have connection to another command control server.
Categorised as: blogmail, Hardware/Software, Microsoft, Networking, Password, Recovery, Server OS
Thank for your help, 99.9% of my files are now back to normal. 2 file I couldn’t open that could be related to different issue.
Thank you. life saver, saved my job.
Thank you. saved my job.
Excellent work, thanks for saving my job, all company file are now restored.
Send you an email. Very critical scenario here.
It was very expensive, learn the hard way now my company have invested in backup system. thank you for your help.
Thank you for your hard work. all file working.
got everything backed up now, as per your recommendation. big lesson. backup, backup, backup.
Be careful – the decrypter tool was infected with “luhe.fiha.a.” Always be sure to perform your recovery on an isolated network.
Are you sure it wasn’t in already in your PC ? As this malware ually spread via attachment & compromised website. But anyway I always recommend everyone to run the decrypter on isolated network or decrypt using private key.
Obviously an isolated network is the best practice for performing the decryption, but are there any ramifications of doing so on a production network (one where there may be a significant amount of data to decrypt?
After analyzing the decrypter executable, it appears that there are no immediate network transmissions using Wireshark, nor file or registry calls outside of the decryption of the actual file.
Anyone?
Everyone on here who has paid the ransom has received the appropriate decrypter tool, correct?
Any issue with
A – reinfection by CryptoLocker or another virus within the decrypter tool?
B – the decrypter tool expiring and demanding more money?
From the looks of things, this thing is more preying on users and companies for extortion, and not malicious in terms of damage/infection.
Everyone on here who has paid the ransom has received the appropriate decrypter tool, correct?
– That’s correct
Any issue with
A – reinfection by CryptoLocker or another virus within the decrypter tool?
– I haven’t had any issue, just to be safe I always running decrypter on isolated network.
B – the decrypter tool expiring and demanding more money?
– That’s correct, but I have seen price going up as well as going down after waiting bit longer, maximum I have seen is 10BTC and min 1BTC.
Regarding point B.
Is there any concern that once the Decryption tool is purchased and download, that it may have an expiration date.
i.e. looking for more ransom?
there is a possibility of expiry and more ransom. There is next version of this ransomware are about to get in circulation via mass spam, and next version will clear volume shadow copy.
Thanks for sorting this for me. All files are now decrypted & working.
Thank you. My files are working.
I got infected last week and I have removed the virus from the infected PC, however the Files on my files server has been encrypted. how do I decrypt these Files
Have you checked your Volume Shadow Copy? if you don’t have backup only way to get the decrypter is by paying the ransom.
I have paid a ransom and downloaded the dercyptor exe.
How do I run it safely and securely?
Can I target which files to decrypt or does it traverse all drives and directories?
Thanks
Best is to isolate them on separate pc and run the decrypter on offline PC, however, from my experience you can open the decrypter and select the folder containing the files.
You should be able to select the folder it will go through all the files & folder.
We have been infected however the virus has been removed. We want to pay the ransom. How do you pay the ransom and get the decryption file without the virus GUI? I have a screenshot of the Private Key.
Public key on its own is no use, you need private key. If you have used Tor then let me know I will send you the .onion link you can verify your file and pay the ransom, if you have trouble send me an encrypted file I will get the cost for you.
Hi Shiraj, can you help decrypt some files for us. we have infected files but not getting the gui to pay a ransom.
Please email me one encrypted file, I can try to find out a crytpolocker server and how much it will cost.
Hi,
We have found the site on Tor and verified a file. Do you know if the price will go up if we try to verify another file? And also is it time specific? The cost is 0.7 bitcoins.
This is the site we went to:
fxxxxxxxh.onion
Can you confirm if this is the correct site and cost?
Thanks.
yes, that is correct .onion site and costs looks ok. Please don’t publicise the site by putting on any forum or blog post, as I don’t think any one should be paying them, as this will encourage them. Have you tried to restore using volume shadow copy or any backup?. I don’t think price goes up based on how many files you verify, I think its based on bitcoin conversion price. Once you get the decrepter make sure you run it on a test PC thats not on your network, copy couple of files on usb and test also check for any other virus not affecting your system.
Thanks for your help.
We, reluctantly, gave the ransom to get the files encrypted. Our problem was the customer’s volume shadow copy was turned off by the virus and we weren’t notified of the virus until the daily backup had backed up the encrypted files.
We got hit and we had to purchase the key & now have the key. It’s not unlocking all the files saying they may be corrupt. Is there another program that can unlock the files if I have the private key?
Shiraj,
I have the private key for our files. How can i go about decrypting the files?? Can you please help or point me on how to do it myself?
Please see windows file system recovery with private key
http://support.microsoft.com/kb/241201
hello, I’m from brazil, got all my company’s server crypted. Can you verify if there is a way to pay for decrypt?
If you send me a copy of encrypted file I can check that for you.
how can i get your email?
“—”
Hello shiraj,
A company of mine has recently feel under the cryptolocker encryption program. I wanted to pay for the private key but without any regards can not find the service center website on TOR. I have tried everything from SC to backups with no luck. The virus has not popped up on my computer and unplugging the NIC did not help. Anyway to get there?
Send me a copy of the encrypted file I will check to see if I can track the server.
I went ahead and sent you a copy. Please let me know how it goes and if I have any luck.
your file looks like is encrypted with Cryptolocker. which TOR site did you checked your file? is that start with f2d2v7?
hi shiraj, I am a personal pc affect by the cryptolocker and some important images encrypted, to pay for the private key is very expensive for me, if any method I can decrypt my files, thanks very much.
Shiraj,
I paid the Ransom and have the “Your Private Key.bin” file saved to my desktop. However, all my files are still encrypted! I can’t open a single one, and it comes up with the usual error file not valid or what not. I downloaded the TorBrowser etc. etc. but my question is… How do I manually decrypt my files using the key!? I don’t understand why my files were not decrypted in the first place. Please help!
Thank You,
Rolando
Shiraj,
Figured it out! Ended up downloading the Free Decrypter from the website and it worked like a charm. Can thankfully say that 100% of my files are fully DECRYPTED and more importantly, now BACKED UP! Now on to taking better preventative measures. Lesson learned. I’m very computer savvy and I slipped up ONCE. That’s all it takes guys. ONE e-mail and ONE click. Hope you guys don’t have to learn this lesson the hard way. DON’T click on suspicious e-mails. And remember to BACKUP your IMPORTANT FILES! Good luck to all!
Best,
Rolando
Shiraj,
I have been recently hit by Cryptolocker day before yesterday. I was not aware of the power of this virus. All my data have been encrypted. First I thought it can be cured, and tried to get it removed using the anti-malware and could get it cleaned… but stil all my data are encrypted. I have lost the URL where we can pay the ransom and get the private key to decrypt the files. Can you please help in figuring out the URL where I can go and try to pay for private key. Please Help..!!!
BR,
Rishi
Do you have access to TOR network? Link only will only works in TOR.
Hi There. Just had my entire company shared drive impacted. Can you please help? who do I email or which of yall knows how to un encrypt? 281-989-1574
If you have good volume shadow copy restore to another drive, Or restore from backup.
Shiraj,
We think we have ran into an issue with this CryptoLocker and it isn’t giving us the pop-up. Can you give me your email in order to send you a file to be checked please?
Thanks for your help!
Hello, Shiraj,
One computer was infected and encrypted our network drive. We have to pay to recover important files. But F-Secure deleted the virus and I have no way to re-infect the computer.
Where to download a copy of the crypto locker? The link left by crypto locker does not work. Or is there any other way to pay?
When employee reported this, I have only 28 hours to go. Please help.
Thanks.
I cannot access to TOR network, can you help?
Are you using link on TOR?