How to recover file from Crypto locker or Ransomware using shadow copy
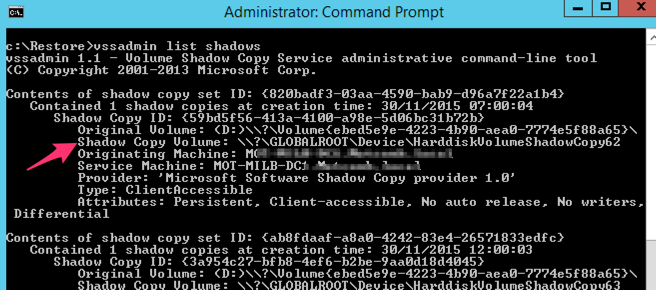
First list all the shadow copy you have using vssadmin list shadows command as below
C:\resources\dosdev\dosdev\x86>vssadmin list shadows
After you run the command if you have any shadow copy it will show the result as below, if you get the result similar to below then download a copy of dosdev.exe, just google ‘dosdev.exe download’ you will need that to mount the shadow copy as drive letter.
Contents of shadow copy set ID: {85e1a1e5-e6dd-4479-ab11-769930317777} Contained 1 shadow copies at creation time: 30/11/2015 7:00:04 AM Shadow Copy ID: {c152023d-6a53-46a5-ae90-eac06d7b1f0d} Original Volume: (S:)\\?\Volume{1d09abf5-50bb-4619-ae1a-582285e37e1f}\ Shadow Copy Volume: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy62 Originating Machine: MACSRVR.mac.macltd.com Service Machine: MACSRVR.mac.macltd.com Provider: ‘Microsoft Software Shadow Copy provider 1.0’ Type: ClientAccessible Attributes: Persistent, Client-accessible, No auto release, No writers, Differential Contents of shadow copy set ID: {b1ceef12-fa9a-4aae-961a-1212df929c27}
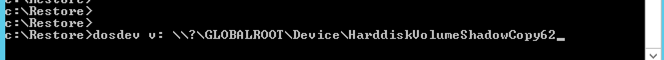
I have underlined the time of shadow copy that I want to restore then copy the path of shadow copy. Navigate to directory where dosdeve.exe is and type dosdev v: then then paste the link you copied, see example below.
C:\resources\dosdev\dosdev\x86>dosdev v: \\?\GLOBALROOT\Device\HarddiskVolumeSha dowCopy62
You should get result as below
v:: The operation completed successfully.
then change the directory to V:
C:\resources\dosdev\dosdev\x86>dir v:
Volume in drive V is Studio1
Volume Serial Number is 18FA-38CD
Directory of V:\
now I have the shadowcopy as drive I can start robocopy, there are different robocopy command you can use 2 examples below, one copy everything other copy only the changes
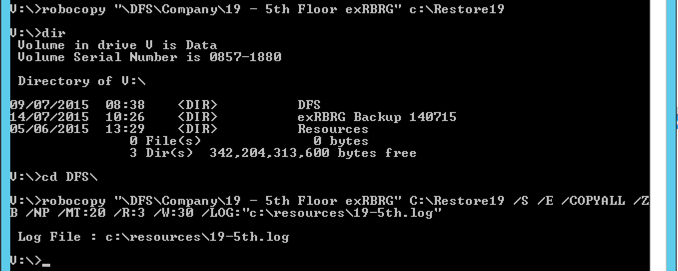
V:\>robocopy “SKETCHUP VERSION 8″ S:\new /S /E /COPYALL /ZB /NP /MT:20 /R:3 / W:30 /LOG:”c:\resources\HR.log”
Log File : c:\resources\HR.log
V:\Studio 1\JOBS\STUDIO\SKYIT\Skyit Rainforest\05_SRR Ede Project\CREATIVE\3D>ro bocopy “SKETCHUP” S:\new /S /E /COPYALL /ZB /NP /MT:20 /R:3 /W:30 /LOG:”c:\resou rces\HR.log”
Log File : c:\resources\HR.log
There is bit more you can do with robocopy the files from your shadow copy.
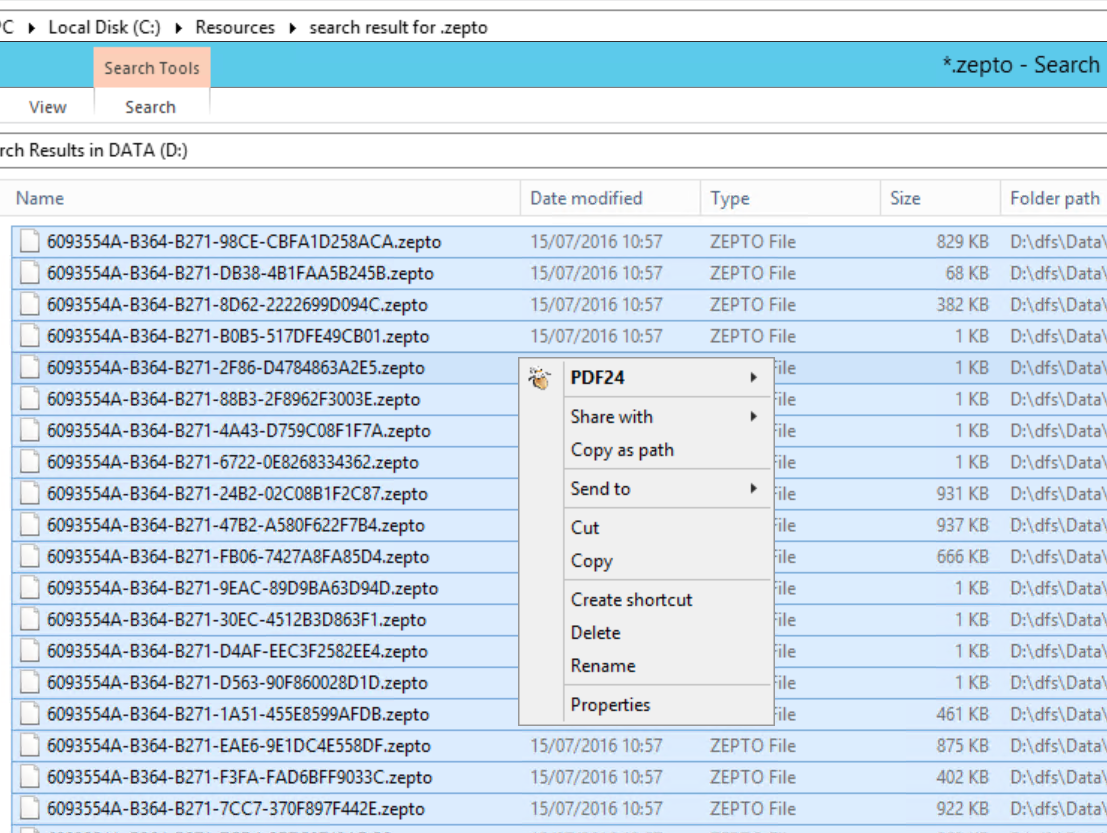
One of my client had Crypto Locker virus with extension .zepto and encrypted number of different directory in shared drive. This is what I have done to recover, first logged on to the server did a search for *.zepto on the top level drive, in my case it was D:\ then I copied the search result to text file, it sound simple to copy search result to text file, if you haven’t done this before then how do you do it. You select the first line of search scroll to last line then ->hold shift and right click -> you get drop down menu select “Copy as Path” then you can open a notepad and paste.
now you have all the path in text file. using the dosdev process as above, I mounted the shadow copy that I want to copy from then run the robocopy command as below,
robocopy /e “V:\dfs\Data\SHARED\PROJECTS” “D:\dfs\Data\SHARED\PROJECTS” /log:c:\project.txt /tee
use this if you have access denied error
robocopy /e /ZB “V:\DFS\WaysOfWorking” “D:\DFS\WaysOfWorking” /log:c:\wayofworking.txt /tee
What this does is check all files and folder copy anything missing or different. I tried going to previous version in windows and browsing the copy then copy the file I needed but for this huge amount of data 10TB, didn’t wanted to do folder by folder also when it hit long file name or path then it stop copying, robocopy is the only way I found to be accurate.
Then I gone back to my search and deleted all the files that ware highlighted.
or you can use command prompt
c:\>del *.zepto /a /s
- c:\>del *HELP_instructions.html /a /s
Categorised as: Microsoft, Password, Recovery, Server OS
Leave a Reply
You must be logged in to post a comment.